Topology

So, in this post we will cover the mtu and fragmentation cases. So, every interface/port have its capacity to send data across the line or port. So, the Maximum transfer unit (MTU).
When I say MTU it usually means at layer 2 frame, but the actual data formation take place at layer 3. So, we have MTU at layer 2 and IP MTU at layer 3.
Bydefault the value of IP MTU is same as MTU, if not defined explicitly. MTU of port may varies depending on the platform or vendor. By default, most of the nodes support 1500 bytes of MTU.
In the above figure, R1 have a maximum capacity payload size(MTU) as 600 byte, while R2 have 300 bytes. It means R1 can send up to 600 bytes in one go, whereas R2 can send 300 bytes.
I hope you getting so far. Bigger the MTU more reliable the network will be. If R1 would have bigger MTU let’s say 9000 bytes and it need to send 800 bytes, it can send in one go, where if the MTU is smaller than the payload then router need to fragment or chopped the packet into smaller size called fragmentation.
So why MTU is significant? This is because if you would have smaller MTU, and you trying to send bigger data, in that case you have to chop the data and send it one by one called Fragmentation.
So, what’s a big deal if fragmentation happen? If your packet is fragmented it won’t stop the communication but overall performance will be degraded.
As Fragmentation is not efficient. Here’s how.
1. Resource utilization: If Payload is bigger than the MTU then router need to fragment the payload. For chopping the actual packet into smaller pieces (fragmented pieces) more resources is utilized. As a result, most of the time router is busy with either fragmenting packet or reassembly it2.
2. Loss of Fragment packet: In case if any of the fragmented packet is loss during the transition, then source need to send all the fragmented packet again. This can degrade the network performance as the same data need to re-transmit multiple times.
So, it is advisable to send packet in one go instead of fragmenting them. We need bigger mtu to achieve this. At this point we can conclude that bigger MTU is good and we should avoid fragmentation in order to achieve better network performance. But it is difficult to maintain uniform mtu throughout the source and destination, as many times the destination is beyond your limit. So, let’s explore some use cases about fragmentation and understand how it works.

In above depicted figure we set IP MTU on R1 as 600 byte and on R2 is it 300 bytes. Now we will try to send data 600 byte from R1 to R2 and let’s see what happens. I will use capture to understand it better.
Now before we proceed let’s look on some of the filed in ip header which play an important role during fragmentation.
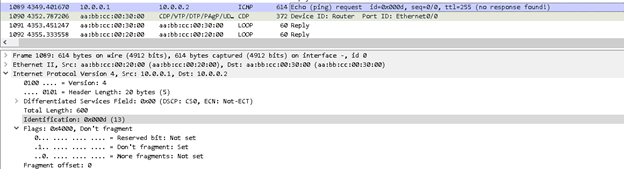
1. Identification: This is 16-bit value, which is used to uniquely identify the payload. So, let’s say Data A has been fragmented into A1, A2, &A3. All Fragmented packet (A1, A2, &A3) would have same identification value.
2. Fragment offset: It is 13-bits value which represent the relative position of fragmented packets.So let’s say if Data A size is 480 byte, mtu is 240 bytes and data A has been fragmented into three pieces viz (A1,A2,A3) then A1 will have a offset 0,A2 will have fragment offset of 0+240=240, and A3 will have fragment offset of 240+240=480. Offset value is always defined in multiple of 8 bytes and it will always start with 0.
3. Flags: IP header have 3 flags, Reserve, Don’t Fragment (DF) and More Fragment (MF)
However only DF and MF field have significance with respect to fragmentation.
If the receiving host receive the payload which is more that its own MTU and if the DF flag in received payload IP header is 0, then it will fragment the packet and accept it.
If the receiving host receive the payload which is more that its own mtu and if the DF flag in received payload IP header is set to 1, then it will drop the packet send ICMP fragmentation needed message.
Are you getting so far? Source Host will do fragmentation when the host need to send payload which is more than its own IP MTU. Receiving host will do fragmentation when the received payload is more that its own MTU and if DF field is not set on the received payload else it will drop the packet.
Case1: In the above figure 2, when router R1 will send payload size 600 to R2 , R1 will not fragment the packet as the Payload at R1 is not more than its own MTU , instead it is equal.
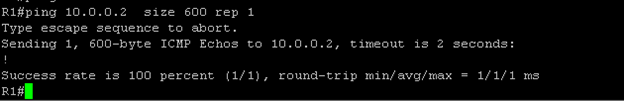
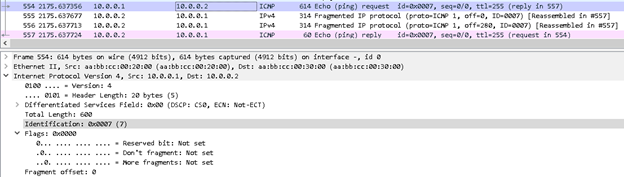
You can see R1 have sent the packet in one go and the DF flag is set to 0, means the remote host is allowed to perform fragmentation on the same. While for R2 it is accepting the packet after doing fragmentation.
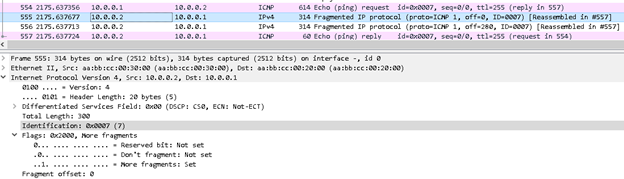
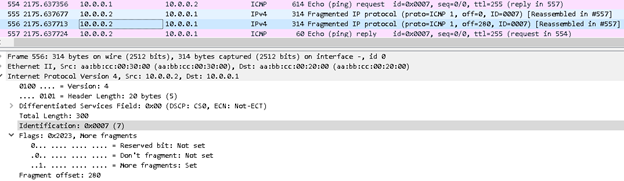
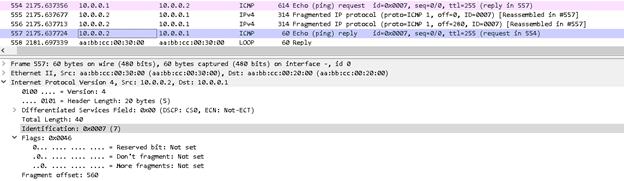
From the above R2 capture you can see that the R2 has fragmented the packet, into three pieces 280bytes + 280bytes + 20bytes. All fragmented packet has same identification field i.e. 0x0007 Each fragmented packet except the last have MF flag set to 0, which denote the sender that it is fragmented packet and more has to come.
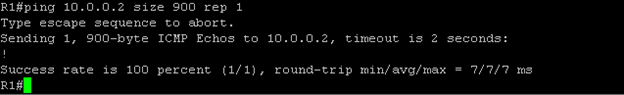
Case2: This time we will create a payload of 900 bytes, which is more than the MTU of R1 & R2. What should happen here? R1 will see the payload and come to know that payload is bigger that its MTU, so it needs to fragment it. So, it will fragment packet into two parts (600 bytes & 300 bytes) Now what will happen at R2 when it receives two packets with size 600 byte and 300 bytes.? R2 will accept the packet with size 300 byte as the payload is not bigger than its MTU, but for 600 byte it will do fragmentation and then reassemble the packet together to see it. Let’s check out in capture.
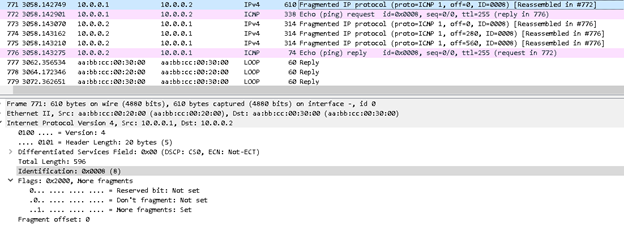
So here you can see the R1 has chopped the packet into two pieces where as R2 has chopped into 4 pieces. This is because for each payload packet header also get added, so actual data is 900 bytes, but as R2 is doing fragmentation do it is adding 20-byte extra header for each fragmented packet which result in four pieces.
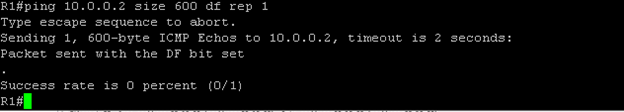
Case3: Lets send payload of 700 byte from R1, setting DF bits, which means we are saying R1 not to fragment the data even if the payload is bigger than its own MTU.
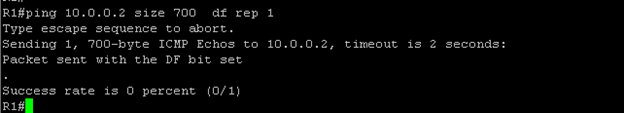
Here R1 refuse to send the payload, as it is not capable to handle payload which is more that its own MTU size.
Case4: Lets send the payload with 600 bytes from R1 to R2 setting DF bit. What should happen? Since the payload at R1 is equal to R1’s MTU, so R1 will be able send the payload out of its interface, but we also setting the DF bit here, which will not allow the R2 to fragments the packet. As a result, R2 will drop the packet.
Summary:
1. Bigger MTU is good for network performance.
2. Fragmentation could degrade the network performance.
3. Fragmentation of packet can happen at any place source, destination or intermediated nodes.
4. Reassembly of fragmented packet can only happed at destination end with the exceptions that no firewall or NAT device exists in the path.
5. If FW or NAT device is placed between source and destination path then reassembly need to happen at FW and NAT devices, this is because FW need to perform DPI (Deep packet inspection) for which it requires to inspect the packet as a whole.
Summary:
- Bigger MTU is good for network performance.
- Fragmentation could degrade the network performance.

Good!