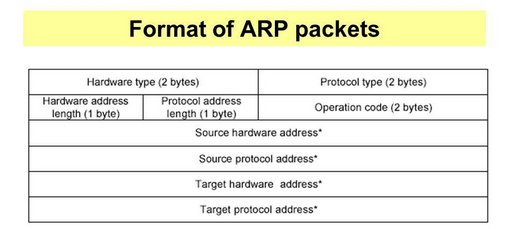
In NSX-T password reset is done through GRUB menu. By default GRUB menu is not enabled.We need to enable GRUB on root mode.To reset password for NSX-T manager first check the NSX-T version that is being in use.
Step1: Enable GRUB menu when you have root password
Step2:Reset password once you have GRUB mode enable
Step3:Enabled GRUB menu when root password is forgotten
The above steps are described in details as below
Step1: Enable GRUB menu when you have root password.
GRUB mode menu enabled by login to root mode. So root mode password is required.
However, if you have root mode password then you can easily reset admin password no need to bother about grub and all. So it seems chicken & egg problem.
Follow below VMware document based on your NSX version to enable GRUB menu.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.0/installation/GUID-4630C9D5-71FB-4991-AC1D-9FDBA0B86120.html
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/installation/GUID-4630C9D5-71FB-4991-AC1D-9FDBA0B86120.html
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/installation/GUID-4630C9D5-71FB-4991-AC1D-9FDBA0B86120.html
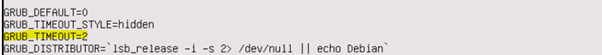
Check if GRUB is enabled or not from grub file located at /etc/default/grub. Note If you see any value Infront of keyword GRUB_TIMEOUT or GRUB_HIDDEN_TIMEOUT it means grub menu is enabled.
Refer below snip
Step2: Reset password once you have GRUB mode enable.
Once you enable GRUB mode then you can easily reset the password following below document. Note you must authenticate with GRUB password before you reset root and admin password.
Each version of NSX-T has its own GRUB password. Follow below link to check GRUB password and reset steps.
In case you forget the root, password, and admin both and want to reset it then the only option we have is to enabled GRUB MENU. Follow below steps to enabled GRUB.
Note: this is not official recommended procedure, the steps mentioned below are taken from website https://thefluffyadmin.net/?p=1455